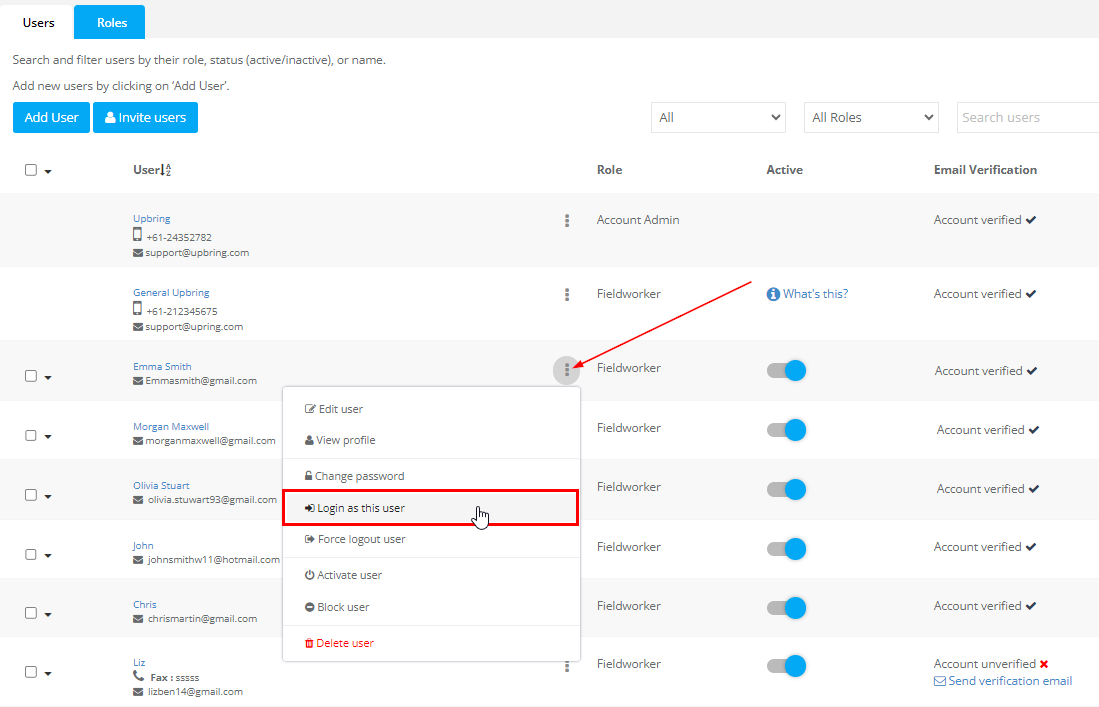
Login as Another User (User Impersonation)
OctopusPro’s Login as Another User tool lets authorised managers temporarily access the platform through a colleague’s eyes—without needing their password. Every click is recorded in the audit trail, preserving accountability in line with security best-practice guidance for impersonation features.
Who Can Use It?
-
Account Owners, Admins, and Delegated Supervisors with the Impersonate Users permission. Limiting this right to specific roles follows the principle of least privilege recommended across SaaS ecosystems.
Access Path
-
Go to Settings ▸ Company Settings ▸ Users.
-
Locate the target user and open Actions ⋯.
-
Click Login as This User.
-
Confirm in the pop-up. You’ll see a coloured banner reminding you you’re impersonating.
-
When done, hit Return to Admin in the banner or from your avatar menu.
Tip: If the target is a fieldworker, you’ll see the same mobile-first layout and menu they see, making it simple to replicate workflow or GPS-tracking issues.
Typical Use-Cases & Benefits
| Scenario | Benefit |
| Troubleshooting a fieldworker’s timesheet sync on the mobile app. | Reproduce and fix in minutes without screen-sharing. |
| Training new office staff on invoicing. | Demonstrate directly in their UI; no sandbox needed. |
| Delegated Data Entry when a fieldworker is off-grid. | Post job notes or upload photos on their behalf to keep jobs moving. |
| UX Research before rolling out a new layout. | Walk through typical workflows from user roles to spot pain-points early. |
| Compliance Audits | Provide auditors explicit evidence that actions were carried out via impersonation, not by the user themselves. |
Security, Privacy & Audit
-
Full Audit Trail: Every impersonated session logs who acted, whose account was used, timestamp, IP, and actions performed—aligning with NIST SP 800-12 audit-trail guidance.
-
Banners & Visual Warnings: Persistent indicators reduce the risk of accidental data entry in the wrong context.
-
Role-Based Controls: Impersonation permission can be withheld from high-privilege roles to avoid circular access issues.
-
Session Timeout: Ending the session or timing out returns you to your own account automatically, limiting exposure.
Best-Practice Checklist
-
Grant impersonation only to roles that genuinely need it.
-
Never share login credentials; always use the built-in feature.
-
Review audit logs periodically for unexpected impersonation activity.
-
Inform staff that impersonation is logged and visible to admins to maintain transparency.
Example Walk-Through
Example: An admin receives a call from Sam, a fieldworker, who can’t mark a booking as “Completed” on his phone.
The admin impersonates Sam.
Navigates to the job and observes that required prerequisites are missing.
Completes the checklist, marks it done, and logs out.
The audit trail shows Admin (impersonating Sam) completed the checklist—keeping the record clean while solving Sam’s issue instantly.
FAQs
Q: Can I impersonate a deactivated user?
A: No. Reactivate the account first to maintain data integrity.
Q: Does the user get notified?
A: Yes, an email or bell notification (if enabled) can inform them for complete transparency.
Q: Can I change audit-trail settings?
A: Only Account Owners can alter log retention in Settings ▸ Security ▸ Audit Logs.
Key Takeaways
Login as Another User provides admins with a secure, auditable way to support fieldworkers and office users without disrupting workflows or exposing passwords. When combined with strict role permissions and clear audit-trail policies, it’s an indispensable tool for any operations team aiming to deliver fast, accurate support.
To stay updated, please subscribe to our YouTube channel.